Most Common Online Security Threats You Should Know About
by Robert Fox
With security threats on the rise every year, it can be a very dangerous world out there in cyberspace. However, we are here to provide you with a list of the most common online security threats you should know about so that you can help keep yourself protected and safe online.
After all, if you think you're safe with just antivirus software alone, you may want to think again - as cyber-criminals are coming up with new ways to steal your personal information by hijacking your computer. Which is why, in this article, we are going to over the most common online security threats.
Want to ensure you stay safe on the web after familiarizing yourself with the most common online security threats? Check out our Online Security Tips - An Essential Guide to Being Safe on the Web article.
Contents
Most Common Online Security Threats You Should Know About

Threat #1: Malware
Short for "malicious software", malware is one of the most common ways for infiltrating your computer and even possibly causing damage to it. Malicious software includes such threats as computer viruses, spyware, adware, worms, and Trojan horses.
What Can Malware Do?
- Delete or alter files
- Steal personal information
- Cause loss of personal information by formatting your computer's hard drive
- Send malicious emails that appear to be sent by you
- Take control of your computer
Threat #2: Viruses

A computer virus is a malicious piece of software that not only can affect one computer without the knowledge of the user but its intent is to spread to and infect other computers as well. Even visiting a website can trigger the automatic download of a virus.
What Can Viruses Do?
- Some can corrupt, steal or delete files
- Disable your computer's security settings
- Cause system crashes and loss of data
- Find personal information like stored passwords
- Display unwanted ads
Threat #3: Spam
Spam in a security context is what we all know to be unwanted messages in your email inbox - junk mail as it is also referred to. In a nutshell, spam is the mass distribution of unsolicited messages, pornography or advertising to various email addresses (easily found on the internet through social media sites).
What Can Spam Do?
- Clog up your inbox with unwanted junk mail
- Provide a vessel for scams, threats to your privacy, malware and fraud
- Contain fraudulent links that once clicked will go to a website and install malicious software on your computer
Threat #4: Botnets
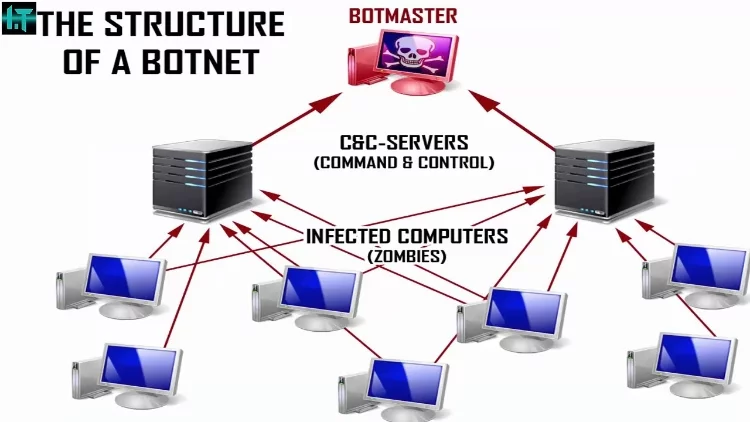
Is a collection of software robots, or bots, also known as a "Zombie army" that are remotely controlled by the originator. These "zombie" computers typically run programs like worms, backdoors or Trojan horses.
What Can Botnets Do?
- Send spam emails that can have a virus attached to them
- Spread various different types of malware
- Can partially attack other computers from your computer using a denial of service attack
Threat #5: Hacking
Hacking is a term that describes the actions someone takes to gain unauthorized access to your computer.
What Can Hacking Do?
- Exploit weaknesses in your computer and exploit them to gain access to your personal information
- Provide backdoor access to your computer and information by installing a Trojan horse

Threat #6: Phishing
Is a common form of spoofing in which fake websites, fake emails, and text messages are produced and look like they are from a legitimate source. However they aren't and are designed to steal personal and financial information from you.
What Can Phishing Do?
- Asking you to update, confirm or validate your account to trick you into giving them your information. Usually presented in an official manner to encourage you to take action
- Cyber criminals are provided with usernames and passwords, allowing them to access your accounts and steal vital information (e.g. credit card numbers).
Threat #7: Worms
Is a malicious software program that can self-replicate and tremendous speeds. It can live in your computer memory and doesn't require attaching itself to programs or files like a virus does.
What Can Worms Do?
- Replicate and send copies of itself to everyone in your contact list
- Wreak havoc on an internal network and shutdown parts of the internet causing damage
Threat #8: Trojan Horses
While you may not be familiar with what a Trojan horse is, chances are that you or someone you know might be or has been affected by one. It is a malicious program that can either disguise itself or embed itself into legitimate software.
What Can Trojan Horses Do?
- Hack other computers using your computer
- Corrupting or deleting your files
- Install malicious programs such as viruses
- Steal information such as credit card numbers by logging your keystrokes
Threat #9: Ransomware
Ransomware is a type of malware that after it restricts access to your files and computer it requires you to make a payment in order to remove the restrictions. Website pop-up ads and phishing emails are the two most common forms of infection.
What Can Ransomware Do?
There are two different forms of ransomware
- Encryption ransomware: which prevents you from accessing files on your computer's hard drive by encrypting them. Can also happen sometimes on USB drives and external drives
- Lockscreen ransomware: that prevents you from accessing your computer by means of an image.
In order to gain access to your computer, the ransomware will display a notification that your system has been locked or encrypted and demands a payment to unlock it.
Threat #10: Spyware
Third parties often use spyware and adware to infiltrate your computer by collecting your personal information without you even knowing. This is usually done in the form of some "free" download and installed automatically without your knowledge.
What Can Spyware Do?
- Collect and send information to third parties without your knowledge
- Can also send valuable information like usernames, passwords, settings, and surfing habits to third parties
- Take you to unwanted websites and frustrate you with uncontrollable pop-up ads
Now that you've familiarized yourself with the most common security threats you should know about, ensure to keep your personal information protected by checking out our Online Security Tips - An Essential Guide to Being Safe on the Web article. After all, you don't want you personal information falling into the wrong hands, do you?
More from my site
 |
 |
 |
 |

About Robert Fox
Rob Fox is a former hydro worker who used to teach self defence in Miami for 10 years. He's currently enjoying his retirement, playing cribbage and golf with his buddies, locksmithing and home security in his spare time. Rob is an avid reader, and has even written a few books on the subject of self defence.
Thoughts on "Most Common Online Security Threats You Should Know About"
 |
 |
 |
 |
Check These Out
You can Get FREE Gifts. Furthermore, Free Items here. Disable Ad Blocker to receive them all.
Once done, hit anything below
 |
 |
 |
 |