IP Address Spoofing – How It Works and How To Prevent It
by Robert Fox
In this article, we will be discussing the concept of IP address spoofing, detailing what it is, how it works, and some methods on how to prevent it from happening.
Contents
What is IP Address Spoofing?
IP address spoofing is a computer hacking technique that involves sending IP packets using an IP source that has not been assigned to the computer which sends them. The purpose may be to hide one's own identity when attacking a server, or to impersonate another device on the network in order to benefit from the services to which it has access.

How It Works
The protocol IP and routing on the internet do not check the source address. This feature of the IP protocol is not a defect but a desired functionality. The IP protocol was designed to allow routing of IP packets to adapt according to network cuts, the reliability of point-to-point links being low in the 1970's. Thus, routers are not supposed to have prejudice over the network origin of the packets.
Except where the access point is restricted to the internet, any computer can make an IP packet with any source address. This technique can be used to mask its real source address or to attack networks by usurping the address of another computer.
To establish a bidirectional link between two hosts, as with the TCP protocol, it is nevertheless necessary that the routing between the two systems is possible. Address spoofing of another subnet may involve altering routing tables of intermediate routers.
Spoofing IP addresses can be combined with denial-of-service attacks on the machine whose IP is spoofed in order to prevent any reply from it, because the machine would send a packet that would invalidate any connection because it has no trace in its system.
It can also be combined with pseudo-random prediction: TCP connections use sequence numbers whose initial value is chosen pseudo-randomly. If the pseudo-random algorithm is too predictable, the attacker may be able to predict the next value from a connection request whose attacker is able to retrieve the response. So it can forge a string of packets that request a TCP connection and that seem to respond to the packets that establish this TCP connection.
For those who like a more visual reference, watch this video to hear IP spoofing explained by Simple Security.
History of IP Spoofing
In 1995, a CERT (computer emergency response team) issued the first warning about IP spoofing.
Indeed, some insecure services such as rship (rocket ship) rely on the IP address to identify the sender. The typical example is to use a trust relationship. An attacker will therefore use the IP address of a trusted (allowed) machine to obtain a connection to a server.
How To Avoid or Prevent IP Address Spoofing

To avoid such attacks, it is recommended that you do not use an IP-based service to identify clients. Cryptographic algorithms can be used to authenticate the correspondent, as is the case for example in IPsec, TLS, and SSH.
It is recommended that the operating system used generates difficult to predict sequence numbers at TCP level. On a computer, the algorithms generating random numbers are always pseudo-random. The deterministic aspect of a computer's behaviour that is why computers are used becomes a problem when security and encryption issues are addressed.
For protocols using multiple TCP connections (such as FTP), it is recommended to use unpredictable port numbers. When the application relies on the system to assign the port number, it is up to the system to implement this recommendation.
One solution may be to reject the successive TCP SYN packets from the same address in order to prevent the pirate from being able to predict the behavior of the sequence number generator. But such a restriction may limit the availability of the service (denial of service attack or DoS).
IP address spoofing can also be used to hide the identity of the hacker during denial-of-service attacks or rebound attacks. In this case, a different IP address can be used for each packet of the attack, making any attempt at intelligent filtering ineffective.
Unicast Reverse Path Forwarding
LAN administrators can use the filtering of incoming source IP addresses of end clients. This can also be accomplished automatically by reverse path forwarding (uRPF), which tells the router to check the routing of the source IP address of any incoming packet by an interface, and if the receiving interface differs from the routing interface, destroy the packet, attempted usurpation inoperative.
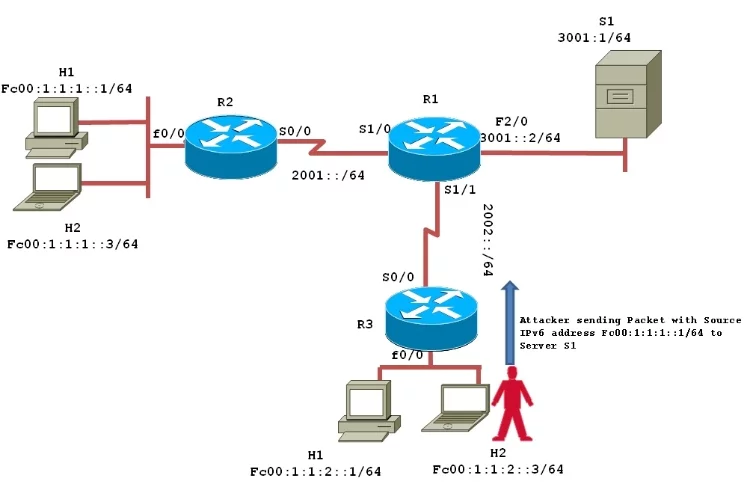
This is not possible with asymmetric routing. This filtering will be more efficient if it is done close to the source. An end user who would like to share outgoing traffic between two links to different access providers would be prevented, with each provider allowing only the expected source addresses.
Here is a video detailing uRPF and how it can prevent IP spoofing.
More from my site
 |
 |
 |
 |

About Robert Fox
Rob Fox is a former hydro worker who used to teach self defence in Miami for 10 years. He's currently enjoying his retirement, playing cribbage and golf with his buddies, locksmithing and home security in his spare time. Rob is an avid reader, and has even written a few books on the subject of self defence.
Thoughts on "IP Address Spoofing – How It Works and How To Prevent It"
 |
 |
 |
 |
You can Get FREE Gifts. Furthermore, Free Items here. Disable Ad Blocker to receive them all.
Once done, hit anything below
 |
 |
 |
 |